PN532 Simulation Campus Card
Foreword
Some time ago, I published a tutorial on simulating a campus ID card, but that tutorial was the most basic and simple. However, it also brought some problems. To ensure safety, mobile phone manufacturers prevent phone NFC from supporting the simulation of encrypted cards. Even if an encrypted card could be simulated, the functions of the encrypted part would be unusable (unless you ROOT the device). In short, the consumption function of the campus card cannot be directly realized through the simulation method described in the previous tutorial. How can this be acceptable! The whole point was convenience, but the consumption function isn't realized? This is unacceptable. Therefore, I consulted a large amount of information, encountered several pitfalls, and, with the support of numerous tutorials, successfully simulated the encrypted card.
I went to the supermarket and bought water this afternoon; it worked quite well.
Screenshots

Preparation
- MifareOneTool Software
- PN532
- NFC-enabled phone
- CUID blank card
- Campus Card
Decrypting the Original Card
- Connect PN532 to the computer
- Open MifareOne Tool
Follow the steps:
- Detect connection
- Scan the card. Cards with SAK 28 or similar cannot be decrypted. The SAK of my school's campus card is 08, which supports decryption.
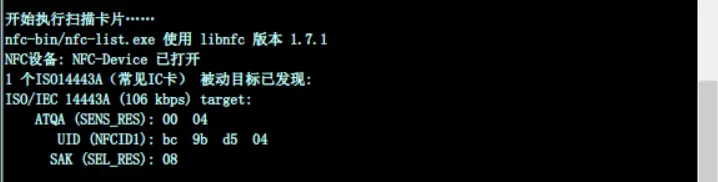
- Detect encryption
- One-click decrypt original card
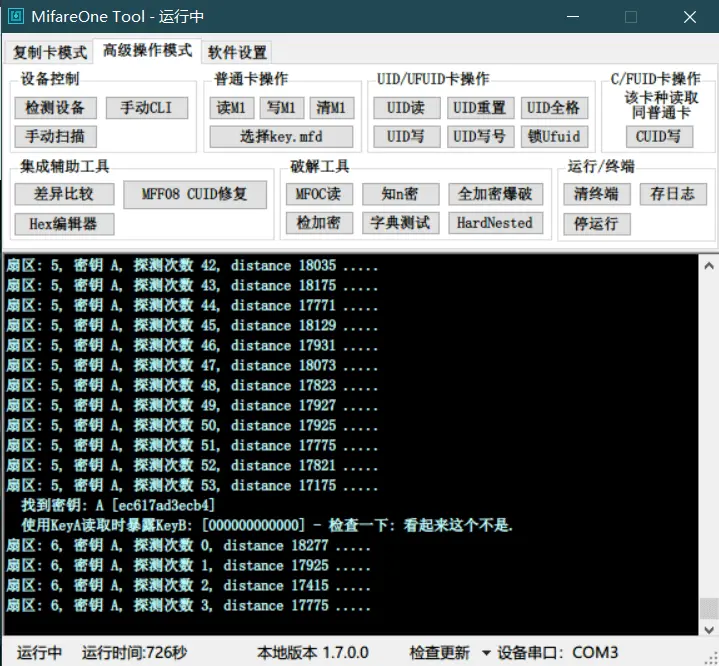
I failed this step many, many times. It took me a whole morning to successfully decrypt the original card data. You can try a few more times; I might just be too unlucky. After successfully extracting the original card data, a window will automatically pop up, asking you to specify the file name and save the decrypted data. The file extension is .dump
At this point, the card is not needed temporarily, so you can remove it.
Writing Data to the CUID Blank Card
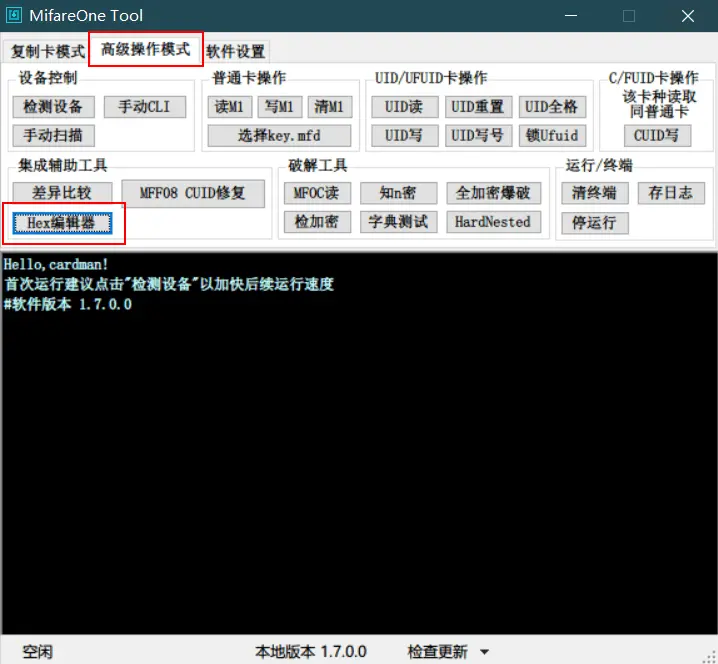
In MifareOne Tool, select the Hex Editor in Advanced Operations mode.
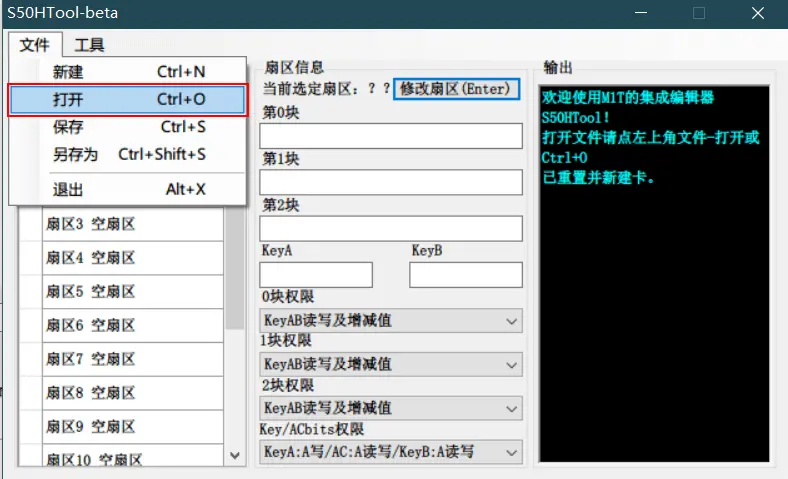
Open the file with the .dump extension you just saved.
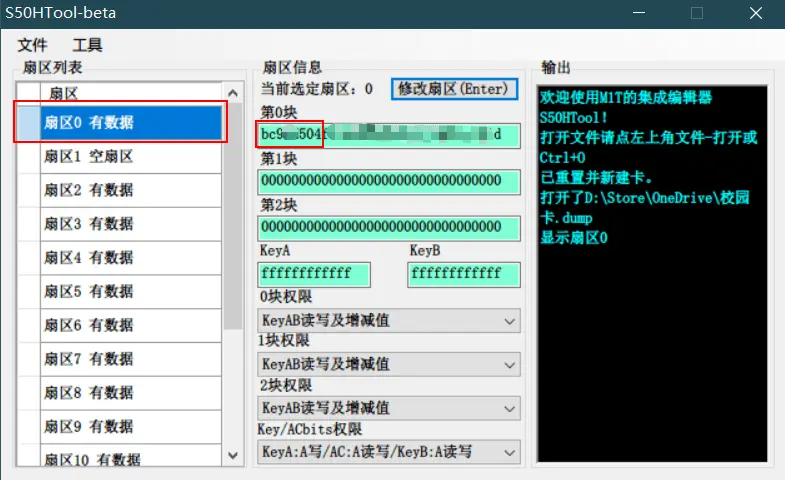
Copy the first eight digits in Sector 0, Block 0. These digits are the Card ID. Alternatively, you can open the .dump file with Notepad and copy the first eight digits of the first line, without spaces.
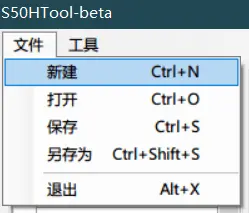
Select New,
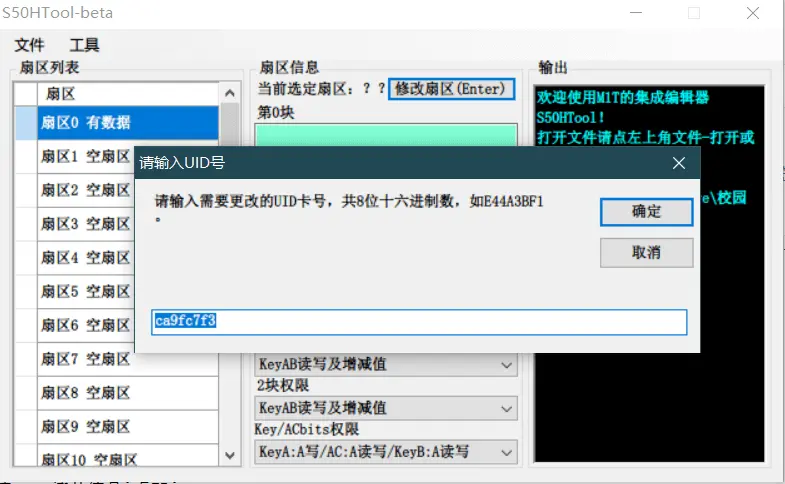
After creating a new file, select Modify UID in the tool, enter the eight-digit Card ID you just copied, then save and "Save As" a file with the .mfd extension.
Place the CUID blank card on the PN532, and go through the steps of scanning the card and detecting encryption.
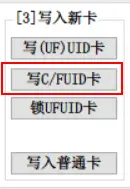
After completing the steps above, select Write C/FUID Card, and choose the file with the .mfd extension! Pay attention to this.
The prompt box below will indicate completion upon writing 64/64. If it shows 63/64, write the CUID card again. This usually works fine.
Then you can use the door card simulation function on your NFC phone to simulate this blank CUID card. You must know that at this point, you have only simulated the Card ID; the encrypted part has not been simulated yet. It is not finished here.
Writing Encryption to the Phone
💡 The tools for this section are the phone, PN532, and MifareOne Tool. The blank card is no longer involved. The mission of the blank card is complete.
Turn on the NFC function on your phone, then place it on the PN532. At this time, the phone will be recognized as a CUID card.
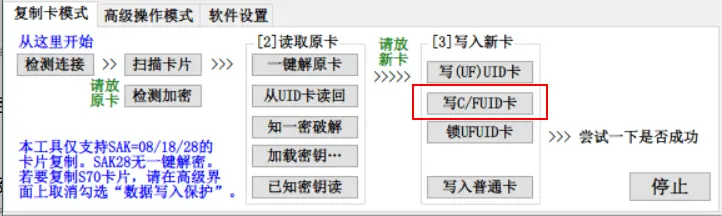
Select Write C/FUID Card again. This time, choose the file with the .dump extension, as this file contains the encrypted card data. The prompt box showing 63/64 written indicates success. The Card ID will not be read again, so this 1/64 will not be successful.
Congratulations, you are finished here. Your phone can now achieve all the functions of the campus card. Similarly, replacing the phone with a wristband in the third part of the tutorial involves the same operation.
